In the previous article, we discussed IT infrastructure security in the outer layers of our security onion: policies, procedures and awareness. This time we are going to go deeper and talk about the next layers which are: physical and network perimeter security.

Physical Security
Physical security is a critical aspect of defending your digital data and IT systems. A successful cyberattack doesn’t have to be conducted from cyberspace like the Internet, it can also be done by unauthorized personnel having access to your physical servers, network, or computers.
To prevent that from happening, we not only need the procedures and policies discussed in the previous article, but also a couple of different additional safeguards, dedicated to mitigating risk associated with theft, vandalism, or sabotage.
The first safeguard that comes to mind when thinking about physical security are security guards patrolling the compound perimeter, and identifying any arriving workers or guests, CCTV cameras often with video analytics technologies, and access control systems such as biometric or RFID card authentications.
Access to your company perimeter should be monitored 24/7 and each room in the company building (depending on the data/hardware it is storing) should be open only to designated staff who can prove their identity.
For example, to get physical access to servers in one of Microsoft’s data centers you, have to pass an extensive multi-layered security check and even if you do get inside where the servers are stored, you are still being supervised by the security team and systems for the entire duration of your visit.
Other physical security measures that are crucial are perimeter fencing, fire suppression systems, reinforced server rooms (working like cages to keep the hardware safe), or even solutions that help you keep your servers operational and mitigate hardware failure possibilities (or help to keep the company running when they occur) like proper AC in the server room, hardware redundancy or backup power supplies.
If you are a small company that doesn’t have a large perimeter, at least choose and implement one or a couple of security measures like CCTV cameras or access control systems, and if you have your systems deployed in the Cloud (or you are thinking about it), make sure to choose a suitable cloud provider that is compliant to all regulations like EN 50600 or ISO 22237.
Some data centers need to be creative in terms of their physical security measures to comply with all manners of regulations. For example, the Polish company Talex has one data center in Wrocław in an old historic landmarked building whose structure cannot be modified due to legal restrictions. To comply with security regulations and enforce their data center building security they had to place concrete flowerpots filled with soil in front of their building that would stop any incoming cars or trucks in case of a terrorist attack.
Perimeter Security
Your network perimeters are all your public-facing services and shore devices (like routers or firewalls). They often fall into three categories:
1. Software as a service:
Those are all your applications hosted in a provider’s cloud, where you only own the data stored on them, but the entire app and underlying infrastructure are managed by the app providers.
In this scenario, perimeter security means properly securing your user accounts via strong passwords, multi-factor authentication, or conditional access policies. Some services have those options built in and others can be secured via delegating access to other identity providers like Microsoft Entra ID (previously known as AzureAD).
2. Cloud environments
Those are all your services/applications deployed as Infrastructure as a Service or Platform as a Service in public cloud providers like Microsoft Azure, Amazon Web Services, or Google Cloud.
In this scenario, we need to first ensure our services’ security via network application security groups (which behave like a stateful firewall, allowing inbound / outbound communication on specified ports and protocols for specific subnets or IP addresses), application security groups (which allow configuring extensive rules for HTTP traffic) and other firewall services with more additional functionalities. Please note that the specific names for all mentioned security options are from Microsoft Azure. Other could providers also provide them, but they may be named differently.
3. On-premises
On-premises infrastructure (the local infrastructure of your office or company) security relies more on properly configured edge devices, so the devices that are on the edge are between your local network and the Internet.
Those devices are your routers, VPN gateways, and firewalls.
The Firewall is the most important tool in securing on-premises networks. Firewalls can come in a couple of versions:
- stateful firewall (the most basic one, which works the same as network security groups mentioned before),
- web applications firewall (used to secure and inspect HTTP traffic, often works similar to a reverse proxy) or
- next-generation firewalls which, additionally to the previously mentioned features, are also equipped with various tools for deeper inspection of traffic (including more layers of network OSI model). For example, they can inspect network packets’ payloads and match them to existing signatures to detect harmful activities such as exploitable attacks and malware.
When talking about exploitable attacks, it is worth mentioning IDS and IPS systems which are often parts of the next-generation firewalls but can also be deployed as separate devices or services:
- IDS (Intrusion Detection System) is a systems that inspect network traffic (often the one coming from public networks) and reports any suspicious founds to the systems administrators or IT security team.
- IPS (Intrusion Prevention System) is a system that inspects network traffic, but instead of only reporting it, it can also act on its own and block the detected attack in real-time. However, they need to be configured precisely because any false positive detections can block legitimate network traffic.
Some notable open source IDS / IPS systems are:
Going back to firewalls, it’s a good idea to deploy a couple of them in your local network. The most often used configuration is separating your local network into two different zones: DMZ (demilitarized zone) and internal LAN. The first external firewall leads to the DMZ and the second internal one to your LAN like this:
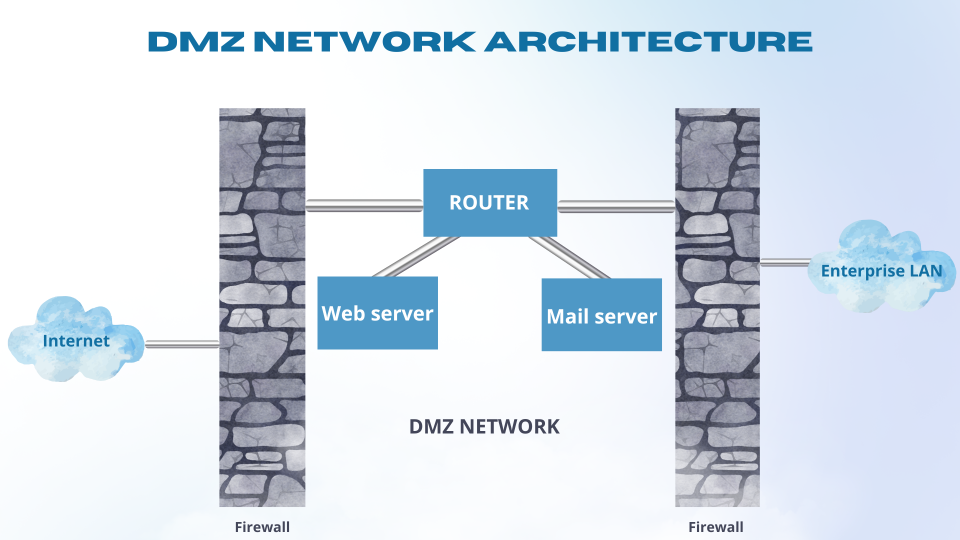
You can place your servers storing nonsensitive data in the DMZ like web servers. The external user will have access to the website that the server is hosting, but will not have access to the database that the server is communicating with (the communication from DMZ to LAN is more strict). This approach allows you to defend from unwanted external users accessing your company data as well as network reconnaissance (it will show only the nonsensitive services in the DMZ).
Summing up:
I hope this article helped you understand how to properly secure your physical and perimeter network security and maybe you learned a new tool or two that will help you achieve it.
In the next part, we will dive deeper into the next layers of our security onion internal, network, and host security, so stay tuned!
Jędrzej Boguszyński
Macrix IT Systems Administrator

