Defending your company IT infrastructure from external or internal threads has become more and more difficult due to the constantly evolving cybersecurity landscape. Moreover, the trend towards moving or expanding company infrastructure to the cloud adds an additional layer of complexity. How can we defend our modern hybrid infrastructure when it can extend over multiple on-premise locations and public cloud providers datacenters? The answer is multiple layers of security measurements!
The security onion model
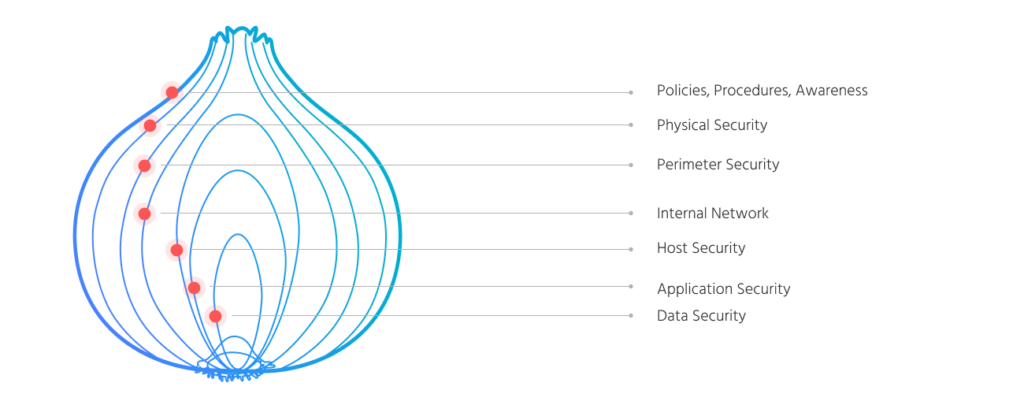
The best analogy about IT Infrastructure cybersecurity is that it’s like an onion. There are many layers and you have to peel each one and make sure there is a proper security measurement at every layer. Even if you think that your data isn’t valuable to criminals, it’s still valuable to you and therefore you need to protect it. Given the wide spectrum of attack vectors that criminals can use, a layered approach to security is crucial.
Let’s look at the security onion layers for a typical company and peel them back one by one. On our way down to the “core” we will discuss each layer and I’ll give you some examples of procedures, technologies and tools that can help secure it.
In this article we will talk about policies, procedures and cybersecurity awareness.

Policies and procedures
This is the outermost layer of the company’s cybersecurity, and it’s related to its operational procedures and employees.
Policies are general guidelines that outline the organization’s (or department’s in a smaller scale) plans for tackling a specific issue and a procedure explains a specific action plan for carrying out a policy.
It’s very important for a company to have policies and procedures related to cybersecurity in place, they don’t have to be created only for a big, urgent matters like ransomware attack.
They can describe how to proceed with guests on the company perimeter, who and when can access the server room, how to securely configure servers or end-users pc, how to configure users account for the onboarding process or how to make sure all access is disabled during the offboarding.
Regardless of your organization scale, developing policies and procedures can help you not only make your organization run more efficiently but also secure every weak points, like poorly configured servers, users getting access to resources without any formal approval or more physical threats like unauthorized people getting access to your company perimeter.
If your company don’t have any formal security policies and you don’t know where to start to create them (or evaluate your existing ones), take a look at ISO 27001 which is as the world’s best-known standard for information security management system. You can check the certification guidelines and tips to help you plan and create your own security policy, tailored to your company.
There is much more documentation online that you can access which can help you create your own policies and procedures (most of them are related to IT security) like:
- Other ISO standards
- SANS Institute security policy templates
- PurpleSec security policy templates
- NIST Cybersecurity Framework
You can also draw inspiration from many real-world security policies that are publicly available like Oracle company security policy, but it must be tailored and modified accordingly to your company needs not only copied and pasted!
A good approach is to go with ISO 27001 guidelines and conduct a risk analysis. It will allow you to identify risks and come up with mitigation methods that often can be described as policies and procedures (or just overall documentation).
An example risk can be an unauthorized actors getting access to your company perimeters, during this risk analysis you can come up with solutions to this issue, like personnel verification by security or just simple supervision of the guest by one of your employees during his entire visit. This solution can further be developed into formal guidelines and procedures which will help you secure your company data.

Employees cybersecurity awareness
“A chain is as strong as its weakest link”, this is why its so important to educate employees about cybersecurity hygiene and popular attack methods like phishing or “evil twin”. You can have the most advanced security measures in place but sometimes all it takes is one employee clicking that “reset password” button in a phishing e-mail.
Your employees’ must be aware on how to detect danger on the Internet and how to protect themselves from it.
The best educating method is performing training and meetups for your employees about cybersecurity. You should focus on topics and threats that the employee can encounter in his daily work or live, like phishing, safety when accessing Open WiFi hotspots or cyberhygiene (e.g. passwords strength and management).
If you have more budget and time you can conduct controlled phishing campaign, where you as the IT department (disguised as external attacker) target your users with phishing e-mails and later use the statistics gained during the testing for further cybersecurity awareness improving.
Of course awareness is not everything, additionally to training and improving your employees understanding of cybersecurity, you must have technical security measures in place for their endpoint PCs which are often an entry point to your internal network.
This technical measurements can be:
- antivirus software (e.g. Windows Defender or third-party software) which will help detecting viruses and suspicious software
- auditing and inventorying software (e.g. eAuditor or Microsoft Intune) which will help you catalog and monitor users’ personal computer, they can also be used to limit apps that are allowed to be installed on the PCs
- firewalls which can minimize the endpoints exposure to public networks, they are crucial and should never be disabled!
To minimize risk you should also stick to the “zero trust” rule, which is a security strategy that assumes individuals, devices and services that are attempting to access company resources, even those inside the internal network, cannot automatically be trusted.
In endpoints the strategy refers to account permissions, user should never have full administrative access to their system or at least he should be always asked if he want to run anything as an administrator (with the need to provide password), this will ensure that if a malicious program is run as the employee’s user on his pc, it will not have administrative right by default and will not be able to do any serious harm before its detected and blocked.
Summing up:
I hope this article helped you to understand why policies, procedures and employees’ cyberawareness should be an important matters for every organization that takes its IT security seriously.
In the next part we will dive deeper into the next layers of our security onion, so stay tuned!
Jędrzej Boguszyński
Macrix IT Systems Administrator

